VPC part3
Class 43rd AWS VPC June12th
Vpc peering
Hybrid Networking
What is the VPN?
Software VPN
Hardware VPN
Direct Connect
Software VPN -demo
DNS Resolution
Firewall: network security for protect the others
Web àrequest(inbound)
172.0.0.0:80 Server
172.0.0.0:15000-65000
ß response(outbound)
Request is the combination of ‘source IP address and the
port number
Response is the combination of Destination ip address and
the port number(Ephemeral port)
Notable well Known port numbers
20 File Transfer protocol (FTP) data transfer
21 File Transfer protocol (FTP) Command Control
Stateful and stateless firewall
A stateful firewall keeps track of the state of active
connections and makes decisions based on the context of the traffic.In AWS VPC
,the primary stateful firewall is security group
Security Groups:
Purpose:
Control inbound and outbound traffic at instance level
Stateful nature:
If you allow an inbound connection, the response is automatically allowed. The state
of the connection is tracked,so the firewall knows that a response to an
inbound request is permitted without an explicit outbound rule.
Rules:
Inbound rules: define
the allowed inbound traffic to the instances.
Outbound rules:define
the allowed outbound traffic to the instances.
Practical
Step1: Created one window instance ccitpublic name , attach the subnet public for the security grp ,So far Security groups , have given All traffic ,it is not good practice to give all traffic
you need give RDP connect
Step2: Connect the RPD Windows instance ,Install IIS Webserver in the window machine
>Server Manger >Add Roles and features
Security group we called as Firewall stateful firewall,inbound you need configure and outbound rule it will handle automatically.
NACL :Network access control list state less firewall ,you need configured both inbound and outbound rules ,then only response will come
Installation completed ,Webserver configure done you can check in c:drive inetpub folder
Step3: Need to check public ip IIS default page will open , before you need open 80 port in the security group
Outside of the server you can able connect using inbound rules, inside server trying to connect any services for ex: internet to connect need set the outbound rules in security group

Linux Machine [root@ip-10-0-1-93 ~]# sudo yum install -y httpd
[root@ip-10-0-1-93 ~]# sudo systemctl start httpd
[root@ip-10-0-1-93 ~]# sudo systemctl enable httpd
[root@ip-10-0-1-93 html]# pwd
/var/www/html
[root@ip-10-0-1-93 html]# vi index.html
[root@ip-10-0-1-93 html]# cat index.html
<h1>Welcome to Linux webpage...!</h1>
[root@ip-10-0-1-93 www]# sudo mkdir -p /var/www/html81
[root@ip-10-0-1-93 www]# sudo cp /var/www/html/index.html /var/www/html81/index.html
[root@ip-10-0-1-93 www]# vi /var/www/html81/index.html
<h1>Welcome to Linux webpage 81 port...!</h1>
[root@ip-10-0-1-93 www]# sudo cp /usr/lib/systemd/system/httpd.service /usr/lib/systemd/system/httpd81.service
[root@ip-10-0-1-93 system]# sudo vim /etc/httpd/conf.d/port81.conf
[root@ip-10-0-1-93 conf.d]# cat port81.conf
Listen 81
<VirtualHost *:81>
DocumentRoot "/var/www/html81"
<Directory "/var/www/html81">
AllowOverride None
Require all granted
</Directory>
</VirtualHost>
[root@ip-10-0-1-93 conf.d]# sudo systemctl restart httpd
You need to open the security group 81 in the inbound rules
We can able give single ip , in security group , we have all ipv4, instead of that give you own ip
i will access webpage that system ip only.
Security group will work only instance level
NACL
state less firewall ,you need configured both inbound and outbound rules ,then only response will come , It is automatically create whenever you created VPC , it is working subnet level, if you are apply any rule,it will apply all the subnets of the corresponding instances.
Step1: Create network ACL >give name ccitncl >choose you vpc
VPC Peering :
VPC 1 (Public subnets,private subnet), VPC 2 (public subnet,private subnet),
you can able to connect public subnet both the vpn,here you need connect public subnet from one vpn other vpn private subnet
A VPC Peering Connection is a networking connection between
tow VPCs that enables you to route traffic between them using private IPV4
addresses or IPV6 addresses
This connection can be established between VPCs within the
same AWS account or across different.
Peering limitations
You cannot create a VPC peering connection between VPCs that
have matching or overlapping IPV4 or IPV6 CIDR blocks
VPC peering does not support transitive peering
relationships.
You cannot have more than one VPC peering connection between
the same two VPCs at the same time
Step1:Created two VPC's (ccitvpc1 and ccitvpc2),As see below two associated subnets created attached internet gateway for public subnet only
ccitvpc1
ccitvpc2
Step2:Create Two subnet's for each VPC total 4 subnets created, ccitpublic-ccitvpc1 for public subnet separate route table created attached VPC added internet gateway
one more subnet ccitprivate-ccitvpc1 for private subnet separate route table created attached VPC not internet gateway added
Step3: Same as above ccitpublic-ccitvpc2, attached vpc and internet gate way one more subnet ccitprivate-ccitvpc2 for private subnet separate route table created attached VPC not internet gateway added
Step4:Created two internet gate ways
ccitvpc-1-internet-gateway attached ccit-vpc1
ccitvpc-2-internet-gateway attached ccit-vpc2
Step4: Create four Route table public route tables need attached internet gateway
Practical
Step1:
Need to create one instance using public subnet VPC1, it has internet gate attached,
Need to create one instance using private subnet VPC2 ,it have not internet gate not attached.
As see here create three instances CCIT-VPC1-PUB,CCIT-VPC1-PVT ,CCIT-VPC2-PUB

Here we plan to connect or ping private instance VPC1 (
i.e CCIT-VPC1-PVT)
from other public instance VPC2 (i.e CCIT-VPC2-PUB)
Public VPC2 instance
Instance :CCIT-VPC2-INST-PUB
Public IPV4: 35.177.15.196
Private IPV4: 10.0.2.14
Instance :CCIT-VPC1-INST-PVT
Public IPV4 : 13.41.186.187
Private IPV4: 10.0.1.36
Public VPC1 instance
Instance : CCIT-VPC1-INST-PUB
Public IPV4: 18.169.188.224
Private IPV4: 10.0.1.22
Step2: As below Public VPC2 instance connected, try to ping other VPC1 instance Private ip 10.0.1.36,getting timed out
PS C:\Users\Administrator> ssh -i "AMAZON-LNX-KEY.pem" ec2-user@35.177.15.196
, #_
~\_ ####_ Amazon Linux 2023
~~ \_#####\
~~ \###|
~~ \#/ ___ https://aws.amazon.com/linux/amazon-linux-2023
~~ V~' '->
~~~ /
~~._. _/
_/ _/
_/m/'
Last login: Sat Jun 14 15:16:44 2025 from 84.225.106.12
[ec2-user@ip-10-0-2-14 ~]$ ping 10.0.1.36
PING 10.0.1.36 (10.0.1.36) 56(84) bytes of data.
timed out
timed out
Step3:As below Public VPC1 instance connected, try to ping Same VPC1 instance Private ip 10.0.1.36,getting resonse, Because of Same VPC, If you are need connect other vpc required VPC peering
PS C:\Users\Administrator> ssh -i "AMAZON-LNX-KEY.pem" ec2-user@18.169.188.224
, #_
~\_ ####_ Amazon Linux 2023
~~ \_#####\
~~ \###|
~~ \#/ ___ https://aws.amazon.com/linux/amazon-linux-2023
~~ V~' '->
~~~ /
~~._. _/
_/ _/
_/m/'
Last login: Sat Jun 14 14:21:10 2025 from 84.225.106.12
[ec2-user@ip-10-0-1-22 ~]$ ping 10.0.1.36
PING 10.0.1.36 (10.0.1.36) 56(84) bytes of data.
64 bytes from 10.0.1.36: icmp_seq=1 ttl=127 time=0.989 ms
64 bytes from 10.0.1.36: icmp_seq=2 ttl=127 time=1.01 ms
64 bytes from 10.0.1.36: icmp_seq=3 ttl=127 time=1.02 ms
64 bytes from 10.0.1.36: icmp_seq=4 ttl=127 time=0.992 ms
64 bytes from 10.0.1.36: icmp_seq=5 ttl=127 time=0.960 ms
VPC Peering
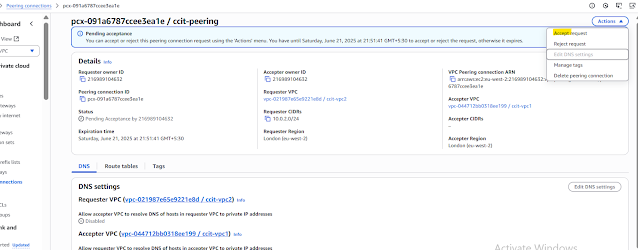
Step1:Create Peering connect select VPC2 and select other VPC1 ,click create peering connetion
Step2: After created you need to accept the request here same aws account ,accept here itself ,if other account wait for confirmation to accept
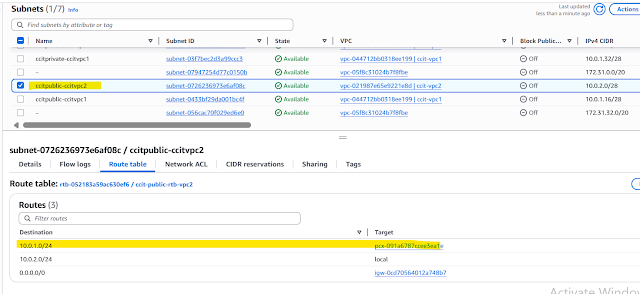
Step3:After Peering active ,need to configure route table of
ccit-public-rtb-vpc2 add the CDR Range of VPC1 for us 10.0.1.0/24,click save changes
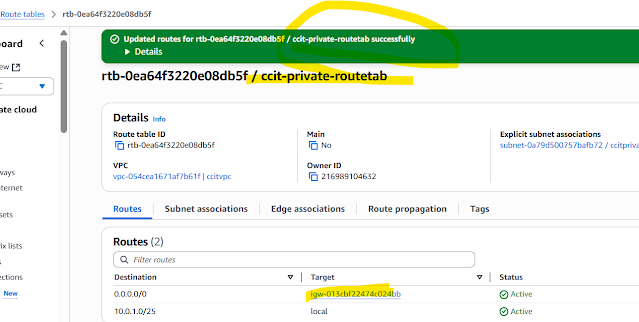
Now you see peering added route table VPC2 public route to VPC1 Private Ip instance Step5: You need one more configuration ,ccit-private-rtb-vpc1, give CDR range of VPC2 click save Now you see peering added via cross route table VPC1 private route to VPC2 public Ip instance
Previous
Last login: Sat Jun 14 15:16:44 2025 from 84.225.106.12
[ec2-user@ip-10-0-2-14 ~]$ ping 10.0.1.36
PING 10.0.1.36 (10.0.1.36) 56(84) bytes of data.
timed out
timed out
After Peering
PS C:\Users\Administrator> ssh -i "AMAZON-LNX-KEY.pem" ec2-user@35.177.15.196
, #_
~\_ ####_ Amazon Linux 2023
~~ \_#####\
~~ \###|
~~ \#/ ___ https://aws.amazon.com/linux/amazon-linux-2023
~~ V~' '->
~~~ /
~~._. _/
_/ _/
_/m/'
Last login: Sat Jun 14 15:50:38 2025 from 84.225.106.12
[ec2-user@ip-10-0-2-14 ~]$ ping 10.0.1.36
PING 10.0.1.36 (10.0.1.36) 56(84) bytes of data.
64 bytes from 10.0.1.36: icmp_seq=1 ttl=127 time=0.970 ms
64 bytes from 10.0.1.36: icmp_seq=2 ttl=127 time=0.964 ms
64 bytes from 10.0.1.36: icmp_seq=3 ttl=127 time=0.962 ms
64 bytes from 10.0.1.36: icmp_seq=4 ttl=127 time=0.934 ms
64 bytes from 10.0.1.36: icmp_seq=5 ttl=127 time=0.980 ms
Previously without peering
VPC2 Public --> VPC1 private Connected Failed
After peering
VPC2 Public --> Peering--> VPC1 private Connected Successfully
Step6:Created one more instance CCIT-VPC2-INST-PVT, now plan to connect reverse way
using same Peering
VPC1 Public --> VPC2 Private
Private VPC2 instance
Instance : CCIT-VPC2-INST-PVT
Public IPV4: 13.41.204.78
Private IPV4:10.0.2.40
Previously without peering
VPC1 Public --> VPC2 private Connected Failed
VPC1 Public connected
PS C:\Users\Administrator> ssh -i "AMAZON-LNX-KEY.pem" ec2-user@18.169.188.224
, #_
~\_ ####_ Amazon Linux 2023
~~ \_#####\
~~ \###|
~~ \#/ ___ https://aws.amazon.com/linux/amazon-linux-2023
~~ V~' '->
~~~ /
~~._. _/
_/ _/
_/m/'
Last login: Sat Jun 14 15:52:15 2025 from 84.225.106.12
Last login: Sat Jun 14 15:52:15 2025 from 84.225.106.12
[ec2-user@ip-10-0-1-22 ~]$ ping 10.0.2.40
PING 10.0.2.40 (10.0.2.40) 56(84) bytes of data.
^C
--- 10.0.2.40 ping statistics ---
11 packets transmitted, 0 received, 100% packet loss, time 10415ms
Step7: need add peering added route table VPC1 public route table to give CDR range of the VPC2 click save
Now you see peering added via cross route table VPC2 private route to VPC1 public CDR range of Ip click save
VPC1 Public --> Peering--> VPC2 private Connected Successfully
PS C:\Users\Administrator> ssh -i "AMAZON-LNX-KEY.pem" ec2-user@18.169.188.224
, #_
~\_ ####_ Amazon Linux 2023
~~ \_#####\
~~ \###|
~~ \#/ ___ https://aws.amazon.com/linux/amazon-linux-2023
~~ V~' '->
~~~ /
~~._. _/
_/ _/
_/m/'
[ec2-user@ip-10-0-1-22 ~]$ ping 10.0.2.40
PING 10.0.2.40 (10.0.2.40) 56(84) bytes of data.
64 bytes from 10.0.2.40: icmp_seq=1 ttl=127 time=1.50 ms
64 bytes from 10.0.2.40: icmp_seq=2 ttl=127 time=1.17 ms
64 bytes from 10.0.2.40: icmp_seq=3 ttl=127 time=1.06 ms
Finally Concept

-Thanks