VPC part4
Class 44th AWS VPC June13th
Hybrid Networking
What is VPN?
Software VPN
Hardware VPN
Direct Connect
Software VPN Demo
Hybrid Networking
- Establish the communication between two different environments
- VPC Peering is the hybrid networking concept in AWS
- AWS takes the complete responsibility of maintaining the peering
- We can create communication between on-premise data center to cloud,cloud-cloud also
- To create communication between on-premise to cloud we need to take the help of come explicit service like VPC(Virtual private network)
VPN(Virtual Private Network)
A
virtual Private Network(VPC) is a technology that creates a secure ,encrypted
connection over ales secure network,such as the internet
it is two type:
i.Software VPN
ii.Hardware VPN
i.Software VPN: onprem-> cloud able connect , cloud ->onprem not able connect
- We need to install a software to establish the communication between the networks
- We should select a public subnet server and install the software VPN as well in the On-premise system.
- The public server works as a central location to maintain the traffic
- The communication establishes over internet using the encrypted tunnels
- We can connect to private servers from around the world using a SW VPN(No location dependency)
- It provides one-way communication only
- For example :Open VPN,Any connect (free service),cisco,AWS client connect.
ii.Hardware VPN
- Here router setup(On-premise) required to establish the communication(encrypted tunel)
- It is a fixed setup works from the office environment only
- It is costlier than software VPN setup
- The communication establishes over internet using the encrypted tunnels
- It provides two-way communication
- For example :aws site-site VPN(s2s)
Direct connect (DC/DX)
- Here AWS provides service over the physical cables. Here internet is not required to setup the communication.
- Not only Ec2-IAM,S3 and all other AWS services we can connect without internet.
- It provides high data transfer as they connected directly over the cables
- The problem with DC is data transfer happen without encryption .We need to take the help of S2S to send the data securely
- It provides two-way communication
Software VPN
AWS Client VPN
3rd Party providers -openVPN ,cisco etc.
Any connect (free service)
Hardware VPN
aws site-site VPN(s2s)
Practical Software VPN
Step1: Create one instance using private VPC,Create one more instance public PVC there we setup VPN
Select Create security group only , don't change that there will be create some protocols for vpn ,not do any change click launch the instance.
ssh -i "AMAZON-LNX-KEY.pem" root@35.177.128.51 --> ssh -i "AMAZON-LNX-KEY.pem" openvpnas@35.177.128.51
it is Agreement , just give yes, after please click enter,enter all enter default yes
You can now continue configuring OpenVPN Access Server by
directing your Web browser to this URL:
https://35.177.128.51:943/admin
During normal operation, OpenVPN AS can be accessed via these URLs:
Admin UI: https://35.177.128.51:943/admin
Client UI: https://35.177.128.51:943/
To login please use the "openvpn" account with "APkByt1I7gxT" password.
See the Release Notes for this release at:
https://openvpn.net/vpn-server-resources/release-notes/
Step 3: admin Connect user name login please use the "openvpn" account with "APkByt1I7gxT" password
https://35.177.128.51:943/admin
and accept the agreement
Step 3: Client Connect user name login please use the "openvpn" account with "APkByt1I7gxT" password
Client UI: https://35.177.128.51:943/
click window install the vpn client locally
Click next and guve user name password "openvpn" account with "APkByt1I7gxT" password.
enable VPN give password more time VPN will connect
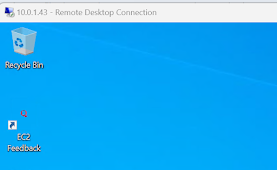
Step4: Now we can take window machine in you local using RDP private ip
10.0.1.43
Private Cloud connect successfully in On-prem machine local, usually database point view we can use this real time
-- VPN Concept completed
Organizations
Introduction
Create Organization
Add and remove accounts
Service control policies (SCPs)
AWS SSO-Identity Centre
Aws Organizations is an account management service that
enables you to consolidate multiple AWS accounts into an organization that you
create and centrally manage.
AWS Organization includes account management and consolidated billing capabilities that enable you to better meet the budgetary, security, and compliance needs of your business.
Introduction
- An organization helps you to maintain all the aws accounts under one account called management account.
- The management account is the parent container for all the added accounts(member accounts).
- You create a policy(service control policy –SCP) to restrict the resource access and apply it to all or selected member accounts in the organization
- An Organization has one management account along with zero or more member accounts.
- An account can be the member of only one organization at a time
- Management account admin has the ultimate privileges to invite new members and remove the existing members in the organization
- Management account is the responsible for the payments of all member accounts in the organization
- We can divide & manage the member accounts in different categories called organizational units(OUs)
- Free-tier feature are applicable with conditions,instead,AWS gives credits to the organization which can share with the member accounts.
Management account can create new member accounts,only emailed enough to create the account as management account takes care of billing activities
No pending bill should remain to the member account in case the account want to come out of the organization
Key point about SCPs:
- SCPs apply to accounts, not individual IAM users or roles.
- Scps set the maximum available permissions for all IAM users and roles in an account.
- If an action is denied by an SCP,no IAM policy can override it.
- Scps are enforced only on member accounts –not on the management account
- AWS Oganizations is an account management service.
- Centraized billing and access management
- Services and regions access can be restricted through service control policies(SCPs)
- Eligible to get credits/discounts from AWS and can share the discounts to the memer accounts.
- Members can be divided into organizational unit (OUS) and maintain the security more flexibly
- Management account has ultimate privileges to add/remove the member accounts and set the SCPs
Practical
>AWS Organizations >Creating an organization>click Create organization
Step1: Below is the my vakatisubbu my management account ,adding one more aws account
Step2: Adding one more account invite the organization using his aws accountid give and click send invite ,the notification send to invited person in the aws organizationStep4: The acceptance will come to you organization, showing accepted
Step5: As see below member account added successfully, now my management account is responsible for the member account , if member account is not paid any bills that bills will need to pay by management account .
AWS Organization >Policies > click enable service control policies.
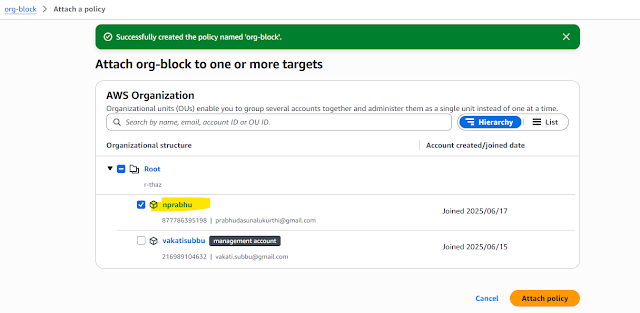
Step7:By default we have Full AWS Access ,instead of the create policy your own,
Give the policy name any :Org-block
Al lservice Choose Organization select Leave Organization policy
Click Add resource and then click create policy After created the policy attach the policy to the member
Step8: Now the member unable to leave the organization ,getting error permission denied
Step9: Using service control policy ,you can control the limitation to the member , for example you want to block S3 bucket
Step10: If you the create group of unit, all members unique policy create group move the user to the group
Step11:give any name Group-unit and click create organizational unit Step12:Click the members action ,move to select the Group-unit ,move account-accountStep14: Which is we have created policy earlier s3, we can attach to group-unit (group)
not individual members, for us only 1 member
is a service that makes it easy to centrally manage access to multiple AWS accounts
Click enable
Step1:Click Create permission sets > give name "permssion-set"select Custom permission set ,choose EC2,S3,im
Step2: added the policy click create, need to add this policy to user
Step3: Create user now , give any dummy email id Click next ,Group(0) click next ,Click add user
Step4:
You need one thing disable Users >setting >multi-factor authentication > configuration select never
click save changes
Step5: with the url username and password ,able to login successfully.
Step6:There above screen shot showing nothin because we are not give any permission to the user
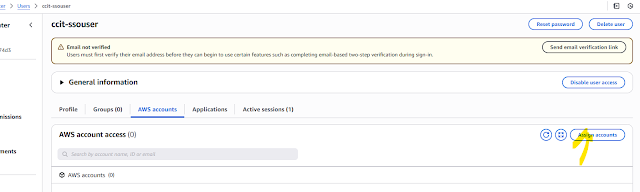
for that click user which we have created and then assign account
now you see nprabhu AWS account user permission given to ccit-sso (identity user)
identity user can use nprabhu memeber policies
Step10: See below given 3 Permission, given to ccit-ssouser identity user (it is single sign on)
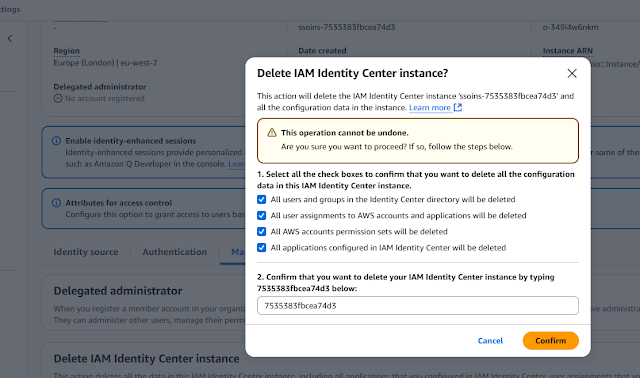
Step12: Complete Identity center you need delete
Step13:Now complete Identity center Organization was delete successfully click confirm.
Getting message like below after confirm
The AWS IAM Identity Center configuration in the Europe (London) region has been successfully deleted. You can enable it again in this or any other supported region
Note: Identity center will be applicable only for the one AWS account not possible multiple regions.
--Thanks








































No comments:
Post a Comment